SQLMap over WebSockets
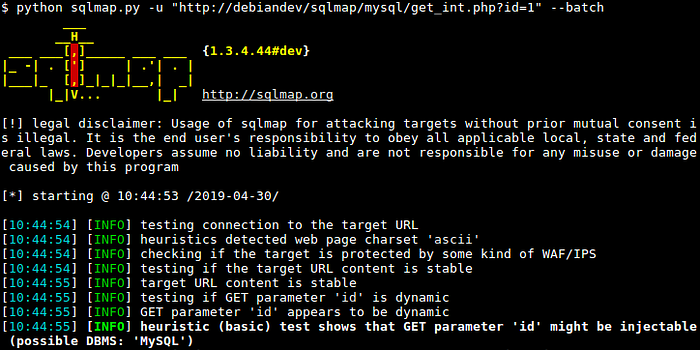
SQLMap is a powerful open-source tool that is widely used for detecting and exploiting SQL injection vulnerabilities in web applications. It simplifies the process of identifying SQLi vulnerabilities, determining the type of database, and extracting sensitive information from the database.
However, there are some limitations to SQLMap. For instance, it may not support certain types of requests, such as those made over WebSockets. Additionally, working with complex targets can be challenging using SQLMap alone.
In this article, we will explore a possible solution to these issues that requires minimal effort and makes also simpler to work with SQLMap.
The idea
To simplify the process the idea is to set up a fake server as an intermediary. With this approach, SQLMap would make a request to the fake server using a common format, and the fake server would then make a more complex request to the actual target.
In this way, SQLMap can be used to test the fake server, which serves as a proxy for the real target. This method can be particularly useful when dealing with complex targets or requests that are not supported by SQLMap.
